In this article we are going to see how to run shell script on the remote
machine using Jenkins and GIT.
The BASH script to restart the service is hosted on the GIT which is a central repository. The Jenkins interact with GIT, download the BASH script onto the target computer and executes.
1) Login to the Jenkins console. Create a new project “Start-Service”.

Make the below configurations to the project.
2) In the General tab. give the project name “Start-Service”.

3) To provide inputs at the run time. Choose check the box “This project is parameterized”.
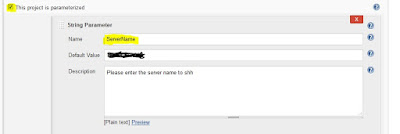


4) I have a BASH script uploaded to my GIT repository to start a service on Redhat server.

The BASH script to restart the service is hosted on the GIT which is a central repository. The Jenkins interact with GIT, download the BASH script onto the target computer and executes.
1) Login to the Jenkins console. Create a new project “Start-Service”.

Make the below configurations to the project.
2) In the General tab. give the project name “Start-Service”.

3) To provide inputs at the run time. Choose check the box “This project is parameterized”.



4) I have a BASH script uploaded to my GIT repository to start a service on Redhat server.

5) In the Build Environment section, we update
the shell execution. Dropdown the Add build step and select Execute shell.

6) Now comes the logic portion for integrating Jenkins with GIT.

The Jenkins build will download the script to start the service to the Jenkins server using git clone and execute on the target server. Here in this example the target server I used have the password less authentication set from the Jenkins server.
7) Run the Jenkins build.


Provide the inputs target server name, user name and service. Click Build.
8) Validate: go to build history and validate the Jenkins build log.


6) Now comes the logic portion for integrating Jenkins with GIT.

The Jenkins build will download the script to start the service to the Jenkins server using git clone and execute on the target server. Here in this example the target server I used have the password less authentication set from the Jenkins server.
7) Run the Jenkins build.

Provide the inputs target server name, user name and service. Click Build.
8) Validate: go to build history and validate the Jenkins build log.








































